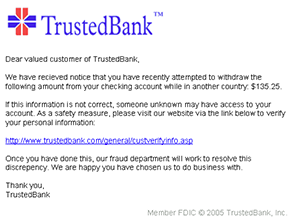
An example of a phishing email, disguised as an official email from a (fictional) bank. Image courtesy of Wikipedia
Phishing is an attempt to obtain private information such as usernames, passwords, security questions, and credit card details for malicious purposes. Phishing attacks happen most frequently via email that appears to be sent from a trusted source. While it’s critical to educate email users about phishing, including how to identify and deflect malicious messages they receive, in many phishing attacks there’s another victim: a legitimate company whose name and identity are being used to send the email.
How should a company or organization respond if their business is impersonated in a phishing scam? Unfortunately there’s not a single method for shutting down phishing attacks, but companies do have a number of ways to fight back.
- Contact your clients and customers by email or snail mail to let them know that fraudsters are impersonating your business. Tell them to ignore suspicious emails that appear to come from your company, and remind them that your business would never solicit private information, such as passwords or credit card info, via email. If your company has a social media presence, use the platform to share details about the scam. The goal of any phishing attempt is to obtain personal data, so letting your clients know you’ve been targeted by phishers can help ensure fewer people will fall for a scam, which may encourage the phishers to move on.
- Contact law enforcement. If you learn of a phishing scam impersonating your business, report it to the FBI’s Internet Crime Complaint Center.
- Learn how to view an email message’s full header, which will be necessary when reporting or forwarding phishing emails to the organizations listed below. A message’s full header will show where the email originated, and it traces the server path from sender to recipient. If you are a gmail user, follow these instructions to view the full header. In Apple Mail, follow these instructions. In Outlook, follow these instructions.
- Forward deceptive messages to the Federal Trade Commission at spam@uce.gov.
- Report phishing emails impersonating your business to the Anti Phishing Working Group, an industry, law enforcement, and government coalition focused on cybercrime.
- Report phishing to PhishTank, a collaborative clearinghouse for data and information about phishing on the Internet.
- If you are a gmail user, learn how to report spam and report phishing, and be sure to do it each time you receive suspicious email.
- If the phishing sender is using a gmail address, report the gmail abuse to Google. If you receive what appears to be a phishing email from Apple, forward it to reportphishing@apple.com. To forward phishing scam messages to Microsoft, email phish@office365.microsoft.com.
- Consumers can file a complaint with the FTC. (This complaint process is just for individuals, not businesses, so you’ll need to ask your clients for assistance.) If your complaint is against a company outside the United States, file it at econsumer.gov.
- If you believe you’ve found a phishing site on the web, report the phishing page.
- Use the phishing episode as reminder to update your company’s security practices. This is an ideal time to review and update your security policies and procedures, including changing passwords and implementing two-step authentication for devices. Contact your internal IT support team, or Connectech, to learn how to authenticate your company’s Internet domain, which will ensure that legitimate email sent by your company isn’t flagged as spam on the recipient’s side. And provide training to all employees and volunteers about phishing scams and how to identify them, so they are less likely to become victims.